Table of Contents
ToggleWhat is BLE?
BLE stands for Bluetooth Low Energy, which was introduced as part of Bluetooth 4.0 Standard. It is aimed at helping low-power-consuming IoT (Internet of Things) and M2M applications within a short range. This was critical in realizing many modern IoT devices which are battery-powered. Like Classical Bluetooth technology, BLE works in 2.4 GHz ISM (Industrial, Scientific, and Medical) bands while inheriting some features from its predecessor with more focus on low power consumption. The maximum power consumption of a BLE application would be around 0.01 Watts to 0.5 Watts, with the same speed as that of classical Bluetooth.
Difference Between BLE and Classic Bluetooth
The main difference between Classic Bluetooth and BLE is in the consumed power. However, there are other major differences due to the architectural differences in each case. The use of 24-bit addresses as compared to 3-bit addressing in Classic Bluetooth allows BLE to connect to 20 connections simultaneously, while Classic Bluetooth only supports 7 connections.
Also, BLE has an upper hand when compared to Classic Bluetooth when it comes to allowable latency in connections. Classic Bluetooth offers a latency of only about 100 ms, while BLE offers an improved latency of 6 ms. Despite, the improved latency, BLE can only offer speeds up to 125 kbps to 2 Mbps, while Classic Bluetooth can offer speeds up to 3Mbps. Finally, BLE can offer only one-way communication with no voice support. Classic Bluetooth has both bidirectional communication capability along with voice support.
How BLE works?
Unlike, Classic Bluetooth, where information is sent continuously, BLE sends bursts of information, thus increasing its time in idle state. For this purpose, BLE uses 40 channels each separated by 2 MHz. Out of these 40 channels, three advertising channels would initially start the connection by sending advertisement packets. The rest of the 37 channels are known as secondary advertising channels and handle data communication.
We can define main three types of nodes in a BLE network, namely:
- Advertiser
- Scanner
- Initiator
An advertiser is a device that transmits advertiser packets. Scanner is the device that receives these packets, without any intention to set up a connection. Now if the scanning device wants to set up a connection, it is known as an initiator. Once, a connection is set up the advertiser is known as the slave while the initiator is known as the master. In BLE, each master and one slave are known as a piconet. However, a single master can form many piconets with different slaves simultaneously. Also, in an equivalent manner, a slave can have many links to more than one master.
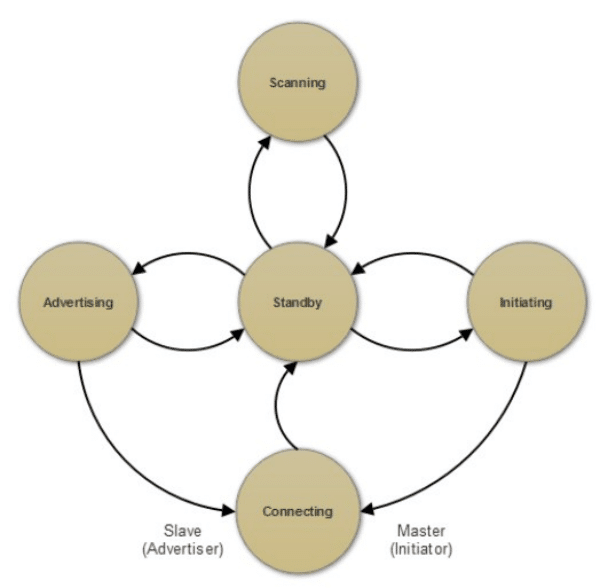
State Diagram
BLE operation is precisely explained using five-link states which define various stages of connection establishment. These states are as follows:
- Advertising state: At this stage, devices transmit advertising packets on advertising channels.
- Scanning state: In this stage devices receive advertising packets without any intention of setting up a connection.
- Initiating state: At this stage, a device intends to set up a connection in response to the incoming advertising packets.
- Standby state: In this stage, devices are unconnected.
- Connected state: During this stage, a connection between the advertiser (slave) and the initiator (master) is set up. Now, the master can be seen as the central device while the slave is the peripheral device.
BLE Architecture
BLE Architecture is structurally like that of Classic Bluetooth architecture, as we discussed in our earlier article. However, the major difference is in the physical layer of the architecture where it can operate in two modes, namely:
- Dual Mode
- Single Mode
In Dual mode, both BLE and Classic Bluetooth can work in harmony in the physical layer. While, in the Single mode only one of them can operate. The choice between the two operating modes solely depends on the application of interest. We will focus more on profiles in the BLE Architecture than its individual components in this article.
What can Tesswave do for you?
Tesswave provide 100+ antenna products and you can contact us for antenna customized solutions, get in touch with us today to get a Free quote.
Get an Instant Quote
Get a FREE quote and we will contact you within an hour
GAP Profile
GAP stands for Generic Access Profile. This profile is important in determining how different devices interact with each other. These interactions come in the following aspects:
- Advertising
- Connection establishment
- Security
In advertising, it is essential for devices to broadcast messages, discover the devices, and to send advertising data. All these operations are overlooked by the GAP profile. Moreover, related to connection establishment it also handles, acceptance of a connection, termination of a connection, and connection parameters. Finally, it is also responsible for initiating and facilitating relevant security measures in the devices.
ATT and GATT Profile
ATT stands for Attribute Protocol and handles defining roles for devices taking part in connection. These roles are defined based on their functionality after setting up a connection. A server is a device that would provide services or resources, while the client is the device expecting resources and services. It is worthwhile mentioning that a slave will not essentially become a server always while the master is always a client. This depends on the purpose of the connection between the two nodes. For example, consider a situation where a BLE connection is established between a wristband tracker and a smartphone. When the tracker sends the heartbeat rate, it acts as the server while the smartphone acts as the client. Now, imagine it is needed to display time on the wristband, for this purpose, the smartphone which has the access to the internet would be the server while the wristband is the client. ATT profile handles provide means for the server to store data in a format that eases different functionalities. For this purpose, ATT profile uses a hierarchical database model.
This is where GATT (Generic Attribute Profile) comes into play. It is responsible for defining the data hierarchy in the database model. For this purpose, it uses a tree-like framework with four levels namely, from top to bottom:
- Profile: This refers to the root node
- Services: These are used for organizing different types of data
- Characteristics: These are the basic storage unit in the tree-framework
- Value and Descriptors: Value is a single value to define a characteristic, while descriptors are multiple values used to define characteristics.
GATT profile can be fully understood by an example. For example, a heartbeat tracker can have following profiles:
- Heartbeat rate measurement profile
- Device information profile
Now let’s consider the heartbeat rate measurement profile, this profile can have the following services:
- Heart rate service
- Body measurement service
So, each of the above services would have different characteristics with values and descriptors as measured by the tracker. For example, heart rate service would have heartbeat characteristics with a value of 69 bpm (beats per minute).
BLE Security
The major types of attacks to which BLE and Classic Bluetooth is vulnerable are eavesdropping and man-in-the-middle attacks. BLE has interesting features to minimize risks due to these attacks. These features are:
- Numeric comparison: Here two end devices would generate a numerical value which will be manually validated once it’s displayed on both devices.
- Passkey Entry: Here the non-initiating device generates a random seed called nonce to authenticate the connection.
- Just Works: Here the non-initiating device generates a nonce with a confirmation value which is confirmed against the other end-devices confirmation value after passing the nonce.
- Out-of-band (OOB): Here the communication is secured over a secondary channel of communication such as Wi-Fi and NFC (Near Field Communication).
Applications of BLE
BLE is a good candidate for Low power PAN (Personal Area Network) IoT and M2M applications. These applications vary from simple home automation systems to large-scale industrial applications. Some of the applications of BLE are:
- Home Automation: BLE has become a popular choice when it comes to home automation applications. These IoT and smart applications include smart sockets, smart locks, smart lights, and smart security sensors.
- Indoor Location Tracking: Despite the availability of technologies such as GPRS, BLE is a more reliable navigation technique due to its performance against interference.
- Tracking applications: BLE is widely used in IoT applications which require only short bursts of information to be broadcasted. This is important in applications such as asset tracking and fleet management.
In conclusion, we can use BLE for IoT applications in PAN networks which require low power consumption and low payload communication.
BLE Beacons
BLE beacons are small transmitting devices that utilize BLE communication technology to broadcast short bursts of messages to listening devices. These are unidirectional battery-powered devices and are widely used in proximity marketing applications and other tracking IoT applications. Currently, there are two famous vendors of BLE beacons, namely:
- Eddystone by Google
- iBeacon by Apple
Conclusion
BLE is widely used in low-power PAN IoT applications mainly focused on home automation applications, tracking devices, and proximity marketing applications. With increasing support for BLE, it is a good candidate for IoT applications that should be ranked high in your choices.